It’s probably their Kanzi cable. As most have said, it’s to perform diagnostics on an iOS device. Bstunt10190-32 points 11 months ago 1 child. Home / Power Repair Tools / Phone Unlocking Tools / SNR Cable USB Serial Number Reader for authorized iOS device SNR Cable USB Serial Number Reader for authorized iOS device Model: SNR01.
Ask just about anyone who uses an Apple product and they will tell you that it is basically impenetrable. Whether it is an iPhone or a MacBook Pro laptop, most consumers rightly believe that their Apple device has a very low probability of getting ‘infected’ by a harmful virus or malware. It is this particular claim that has triggered cut-throat competition for Apple – to the extent that some lines, both legal and ethical, are starting to get blurred.
Digital Crowbar
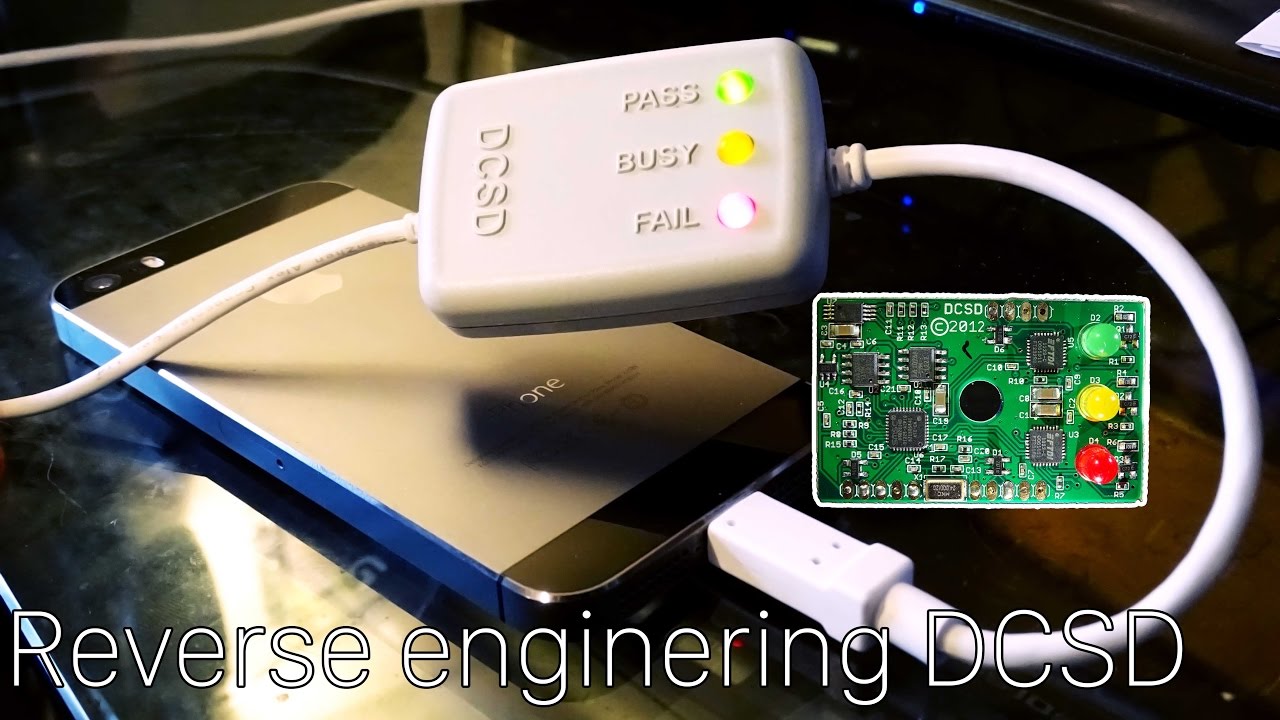
Kanzi Cable Iphone Ditch Witch 5010 Service Manual Sync Google Calendar With Outlook Mac Outlook For Mac Fallout New Vegas Windows 10 Crash Z3x Smart Card Driver Savita Bhabhi Pdf Hindi Online Scania R420 Manual How To Connect Two Wired Speaker To. Some of the compatible devices are iPhone X, iPhone 8, 8 Plus, 7, 7 Plus, Samsung Galaxy S9, S9 Plus, S8, S8 Plus, S7, Note 8, Note 7, Note 5, Note 4, Huawei, LG G5, G4, G3, iPad and etc. Completely waterproof and Warranty: IPX7 waterproof level can easily resist sweat and rain, and you don’t have to worry even if it rains. They are perfect. IPhone debugging requires proper tools. The Bonobo cable connects to your target through Lightning and allows CPU debugging through JTAG/SWD using OpenOCD + AArch64 GDB. Among others, you can: access all CPUs and registers, single step, put hardware breakpoints, dump memory, etc. Perfect for security research. The target serial console can be accessed on the.
According to Lorenzo Franceschi-Bicchierai, technology journalist, hacking into Apple’s iPhone is like trying to break into a black box. Franceschi-Bicchierai, who spent months investigating the secret iPhone phenomenon for Vice.com, says that these dev-fused iPhones are extremely valuable for iOS hackers. There are entire companies dedicated to cracking iPhones for a substantial fee. In addition to hackers, law enforcement officials and security professionals from around the globe request iPhone-cracking services on a daily basis. Essentially, everyone who does security research on iPhones has them.
What’s the Deal?
These “special iPhones”, dev-fused iPhones, have security features turned off or the user can turn them off as fewer core security features are enabled. Franceschi-Bicchierai says that for a researcher it is easier to find infosec vulnerabilities on a dev-fused iPhone than an ‘off-the-shelf’ model. These devices still require specialized knowledge, and using them is still a complicated task. However, Franceschi-Bicchierai remarks that it can be done because it’s like ‘breaking into a house where the lock is already broken’.
Reminder: These iPhones were never meant to leave Apple’s production facilities in the first place.
“Insidious Companies”
The sale of these phones on the grey market is an open secret in the infosec community. Some times all it takes is a direct message on Twitter to one of the many anonymous dealers. Industry insiders do not like to talk about it. Getting ‘root’ access to an iPhone allows researchers to locate vulnerabilities or bugs that can be used by law enforcement agents and governments. Companies like Australian-based Azimuth provide exclusive hacking tools and their customers often include the UK, the USA, and Canadian governments. Another company mentioned in Franceschi-Bicchierai’s investigation, Cellebrite is a forensic services provider that also offers devices that unlock iPhones. In the story, multiple sources have indicated that Cellebrite uses dev-fused smartphones to create their proprietary devices.
Simple Math
Dev-fused iPhones can cost anywhere from $5,000 to $20,000. The final price depends on the phone’s model as well as the particular features or security aspects it contains. It is not enough to get your hands on the dev-fused version of the iPhone. To truly have a ‘behind-the-scenes’ experience, you will need Apple’s special USB cable known as “Kanzi”. After buying the cable, which costs about $2,000 on the grey market, you will need a Mac computer to gain root access to the smartphone.
Mum’s the Word

In the off-line world, many aspects of the special iPhones remain shrouded in mystery – from the total quantity to their point of origin. Apple maintains complete secrecy on the matter. It is also unclear whether it is legal or not to own dev-fused iPhones. Dev-fused iPhones are smuggled out from Shenzen’s electronics market though few are sure how they get from the factory to there in the first place.
Apple’s core marketing strategy revolves around (and has always been about) designing and selling secure, hack-proof and bug-free premium technology products. The presence of these special iPhones and related switchboard devices messes up Apple’s entire ‘our phones are more secure than Android’ assertion.

https://twitter.com/laobaiTD/status/1026546353319493632
If bit 1 is set, SoC has Production production mode, otherwise Development
Kanzi Cable Iphone 11
cpu CPU0
halt
Usually it prints register dump:
reg pc 0x41414141
load path_to_file address
For example, when I installed Whitetail scripts along with Electric Astris, I had issues with GDB debugging